Crytek – The Egregor group has claimed another victim in a series of cybersecurity attacks that began in September 2020. The victim in question is a well-known game developer and publisher. It has been confirmed that the Egregor ransomware gang breached their network in October 2020.
As a result of the attack, many systems and files were encrypted, customers’ personal information was stolen and later leaked on the dark web. The company spoke about the attack in a letter sent to affected parties earlier this month.
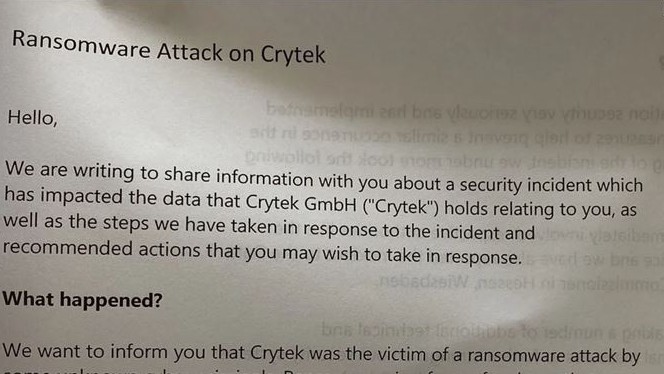
Thanks to BleepingComputer, we can see the contents of the letter:
Crytek has tried to downplay the impact of the data breach, saying that “the website itself was difficult to identify […] so we estimate that very few people will be aware of it”. Not only that, but it was also assumed that the download of the leaked data would have taken too long, and those who tried to download the stolen data were deterred by the “huge risk” that they could compromise their systems with malware embedded in the leaked documents.
Weak arguments and system, brutal attack
I mean, that’s all well and good, but don’t virtual machines exist for a reason? Not to mention that the author of the BleepingComputer article also raises a valid point that such threat actors tend to sell this data to other cybercriminals. Let’s look at what happened to CD Projekt RED when involved in their cybersecurity incident.
In any case, the data Egregor included on their data leak site included the following:
- WarFace related files
- Crytek’s deleted Arena of Fate MOBA game
- Documents containing information about their network operations
In case you were wondering, yes, the infamous group has attacked other game companies as well. Ubisoft was among the victims, having been affected back in October 2020. The group shared files that suggested that they had the source code for the Watch Dogs: Legion and Arena of Fate games that were being made at the time. However, the authenticity of the alleged source code has not been proven.
Egregor itself is known to have attacked several companies with their ransomware. They were threats that exploited the sudden mass dependence on digital infrastructure caused by the COVID-19 epidemic. Considering that some of their attacks have targeted the healthcare sector, it makes even more sense to fear them (or hunt them down – ed.)
The ransomware itself is a modified version of the Sekhmet ransomware and the Maze ransomware. The attacks are characterized by brutal yet highly effective double extortion tactics. According to UpGuard, the cybercriminal group hacks into sensitive data, encrypting it so that the victim cannot gain access. They then publish a subset of the compromised data on the dark web as proof of successful exfiltration.
The victim is then left with a ransom note instructing them to pay a set amount of money within three days to prevent further publication of personal data on the dark web. Or, you know, possibly sold to other criminal organizations. If the ransom is paid before the request expires, the seized data will be fully decrypted.
I highlight all of this information to show that Crytek’s attempts to downplay the incident are far from over. This was a significant cybersecurity attack that threatened the data of many of Crytek’s customers. For now, it’s best to continue to keep a tighter grip on your data. That kind of data is valuable to many people, and you probably don’t want it falling into the wrong hands.
Source: WCCFTECH
















Leave a Reply